The role of PA DSS gap assessment – An overview
Payment Application Data Security Standard (PA DSS) is undertaken by the Payment Card Industry Security Standards Council (PCI SSC). It applies to software vendors and various payment application developers who store, process, and/or transmit cardholder's data for payment authorization and settlement to third parties. PA DSS framework is tailored to ensure that all software developers create secure payment applications. All such vendors need to procure a compliance certificate for PA DSS from PCI SSC.
What is PA DSS Gap assessment?
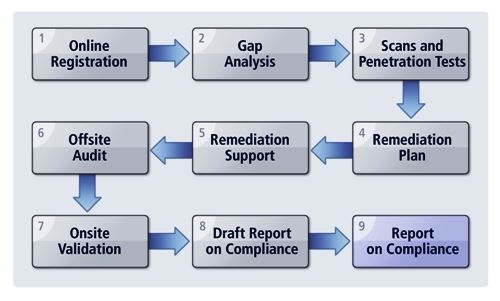
Complying with the standards laid down by the PCI SSC is a very complicated and cumbersome process. This burden can be reduced by a PCI DSS Gap assessment. To this effect, A PA DSS gap assessment aids in identifying, analysing, and documenting the areas of non-compliance with the (PCI DSS).
Gap assessments are the first step towards compliance and determine what the payment application developer is currently doing and what they should be doing to be compliant. These assessments are usually undertaken by or outsourced to security consulting companies. These consulting companies go onsite and check the readiness and provide assistance for an actual PCI assessment.
The 12-step PA DSS Gap assessment checklist
- Install and maintain a firewall to protect cardholder data
- Acceptable password use - Do not use vendor-supplied default passwords
- Protection of stored cardholder data
- Encrypted transmission of cardholder data across public and private networks
- Usage of up-to-date antivirus software
- Maintain a secure system and applications
- Cardholder data must be made accessible on a need-to-know basis
- Assignment of unique system login ID for every employee with accessibility
- Restricted physical access to cardholder data
- Constant tracking and monitoring of all access to network resources and cardholder data
- Periodic testing of security systems and processes
- Maintaining a policy that addresses information security